No matter whether your organization has a considerable, very well-set up 3rd-celebration ecosystem or is in the early levels of building 3rd-party relationships—or wherever between—our managed solutions product will let you Enhance the health of your Firm’s system, together with threat profile and compliance.
Third-occasion possibility assessments are A necessary TPRM procedure, and the top threat assessment workflows will require a few phases: research, conducting periodic cybersecurity danger assessments, and refining hazard evaluation approach.
Leverage engineering solutions to combine procurement, general performance and possibility management over a unified platform6
CISA aids people and corporations communicate present cyber developments and assaults, manage cyber threats, fortify defenses, and implement preventative measures. Every mitigated danger or prevented assault strengthens the cybersecurity of your country.
Distributors have built development in direction of “Secure by Default.” For the solutions and variations CyberRatings analyzed, if a vendor’s pre-outlined high stability configuration is selected, then firewall evasion defenses is going to be on by default. For other stability configurations evasion defenses might not be enabled by default.
Opt for a possibility administration framework to assistance productive remediation initiatives and waive detected dangers that do not implement towards your objectives or considerations.
org. The product’s capability to satisfy its commitments to people is incredibly solid. An item rated ‘D’ is actively remaining breached by recognized threats and is also not able to guard consumers. Ratings supply ahead seeking steering on an item’s ability to satisfy long term commitments. Examination effects included protection success, performance, TLS/SSL performance, management, and client opinions.
”eight Presented the escalating scope and complexity from the TPRM, as the final move from the TPRM methodology indicates, an integrated IT-enabled System would serve the TPRM objectives best.
Cloud security specialists guide the requirements from the cloud when it comes to memory, security, and any possible vulnerabilities that have to have patching.
Streamline vendor onboarding and assessment processes, improving inside efficiency and lessening operational charges.
Common ways of examining organizational and 3rd-get together stability are time-consuming and source-intense. Because of this without an adequate finances and team, quite a few companies are unable to accurately Examine the toughness in their cybersecurity controls.
Dropped your password? Please enter your username or electronic mail tackle. You'll get a url to create a new password by using e-mail.
This guide has everything you need to know about Cyber Ratings conducting an facts stability danger evaluation questionnaire at your Firm.
Companies now trust in expansive world-wide supply chains for all the things from production to digital products and services, abilities, and innovation. Although advantageous, these 3rd party ecosystems are amazingly complex and prone to disruptions.
 Michael Fishman Then & Now!
Michael Fishman Then & Now!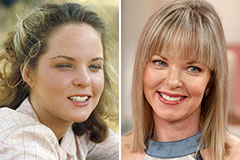 Melissa Sue Anderson Then & Now!
Melissa Sue Anderson Then & Now! Traci Lords Then & Now!
Traci Lords Then & Now! Jane Carrey Then & Now!
Jane Carrey Then & Now! Erika Eleniak Then & Now!
Erika Eleniak Then & Now!